In the cybersecurity realm, there are a tremendous amount of new technologies, methodologies and raising techniques, trying to rival against the indefinitely evolving cybercrime threats. In this post, I will discuss what are Indicators of Compromise and why they are important in threat information sharing.
Indicators of Compromise
One of the rapidly advancing domains in Cybersecurity, is Security Intelligence, which could be defined as a set of processes, policies and tools designed to gather and analyse information coming from diverse data sources in a goal of helping produce actionable information and therefore lead strategic decision making when it comes to cyber-defence. One of the critical pieces of a Security Intelligence environment is threat information sharing. And, if we dig a little deeper, we will discover how Indicators of Compromise or IoCs are the key elements for a successful threat information sharing process.
Indicators of Compromise are items of forensic data (like information found in event logs and network flows), that highly indicate conceivably nasty activity in a given organization’s system.
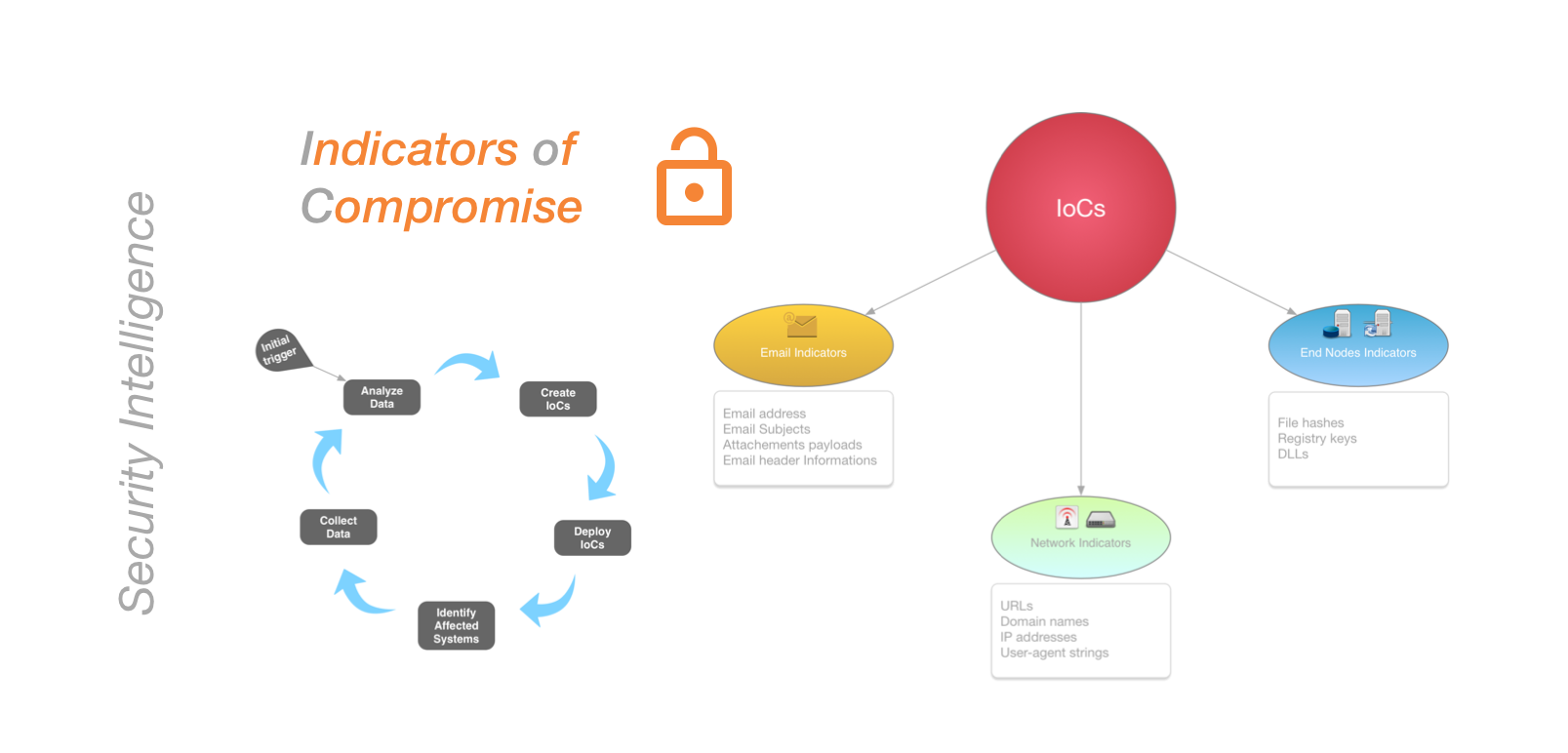
IoCs examples may include pieces of information such as unfamiliar network traffic, unusual privileged account activity, login irregularities, abnormal database read volume, etc. We can categorize IoCs in different clusters as shown in the figure bellow:
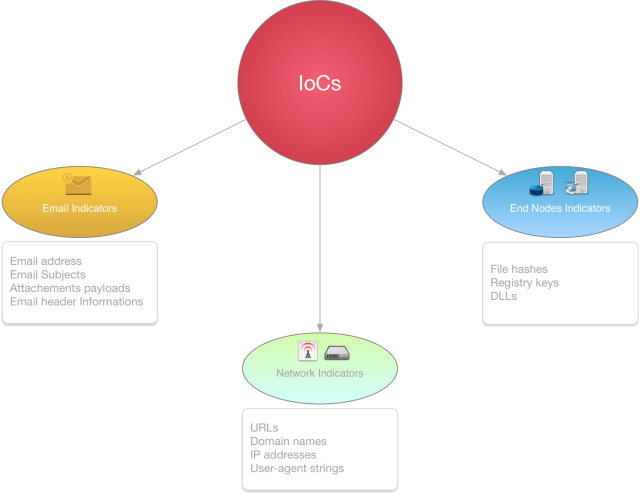
These kind of information play a crucial role when sharing threat information with your peers as a Security Intel adopting organization. Now if we try to picture the importance of such notion in cyber defence, the first thing that comes to mind is the ability of automated threat information sharing.
Automated Threat Information Sharing
Automated threat information sharing or more broadly Security Intelligence Information Sharing is key for helping cyber security specialists to be proactive and well prepared for all possible Advanced Persisting Threats (or APTs). Information exchange could be guaranteed via new emerging protocols specifically designed for that purpose, like the Trusted Automated Exchange of Intelligence Information (TAXII), which is a set of specifications designed to support this kind of data transfer. The data that should be transferred would be embodied in a consistent language like the Structured Threat Information Expression (STIX) that enables standard representation of Security Intelligence data. Now to get back to our main subject here, among security intelligence informations that could be automatically shared between organizations, we will find IoCs.
IoCs sharing is an important aspect of Security Intelligence because they offer the security analyst relatively reliable, aggregated information about logical assumptions that could be tested in his monitored environment and help him depicture possible threats, and maybe in a better outcome, enable informed and strategic business decisions.
But why are IOCs valuable?
IOCs are significant for three main motives. Primarily, IoCs allow threats to be predictable in a coherent manner. If a context is used to document IoCs using common language, it would be conveniently spread among the enterprise security personnel and other external entities. Thus, allowing your peers to participate in the investigations with less communication hassle.
Next, IoCs give threat analysts a collection of data that can represent the raw material to feed to correlation engines to produce automated actionable insights. Therefore by automating this process, we can reduce the time to recover or in best cases proactively stop a threat from becoming an attack, based on the continuum of IoCs lifecycle. A good example of this scenario, would be an IP reputation feed (a largely used IoC) that can be given to à SIEM to automate spam detection based on information retrieved about the IP from an external Threat Intelligence Source.

And finally, IoCs can provide some answers that, as security practitioners will help us assess threats via environment introspection:
- Is that file evil?
- Is that IP a spammer?
- Are we alone?
- How did we get here? We have been breached!
In other words, IOCs are not a fairy’s wand that could save us from the dark side, although they represent a credible source of insight and a good starting point for further research. However, indicators require context to be practical, because with no context to fit in, IoCs would be just the pixie dust of a CISO marketing scheme.