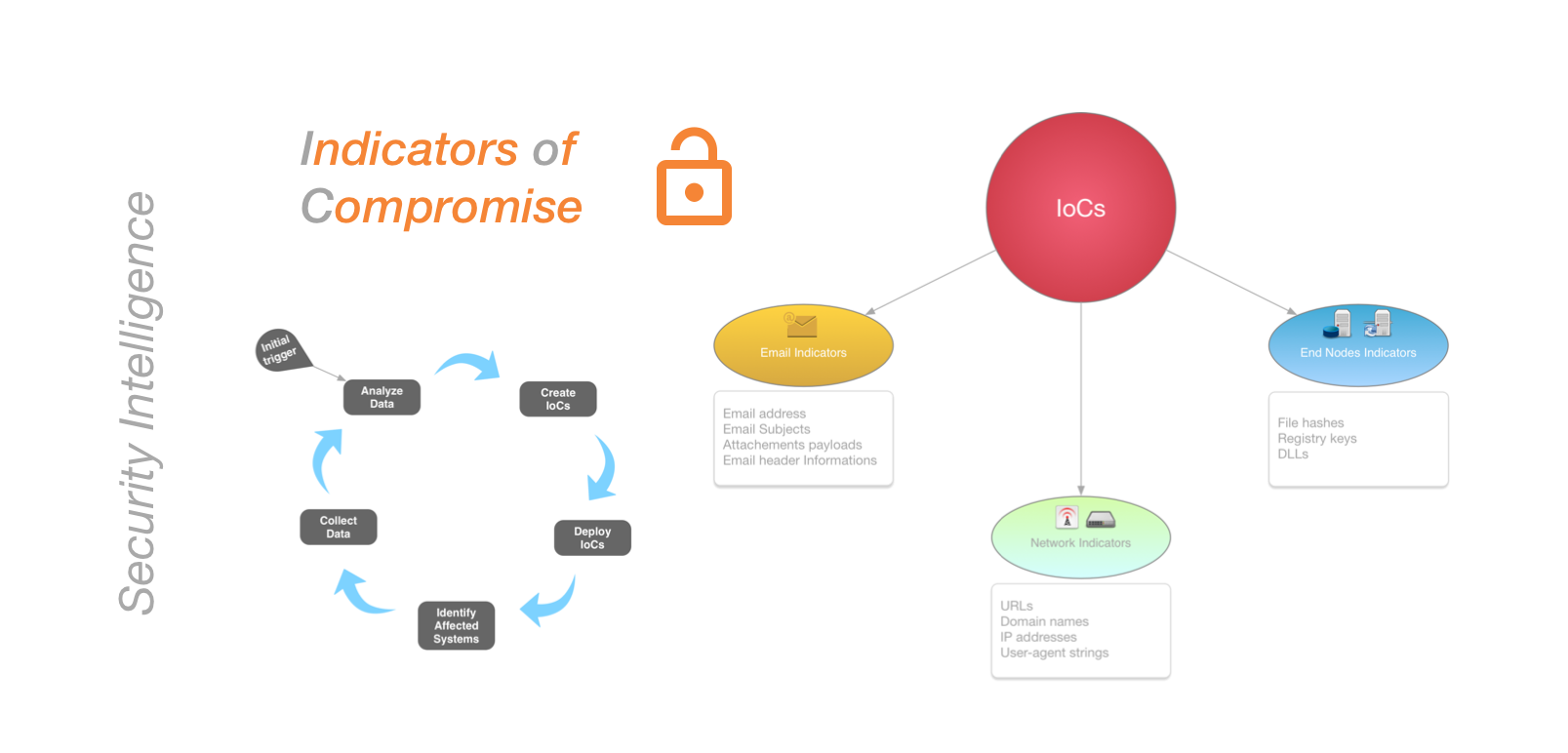
Unraveling the SolarWinds Cyber Espionage: A Cyber Storytelling
Explore the intricate SolarWinds cyber espionage in our detailed analysis. Delve into the sophisticated attack methods, prevention strategies, and key cybersecurity lessons learned from this landmark incident. Ideal for IT professionals and cybersecurity enthusiasts seeking in-depth insights.