How to actually implement Threat Intelligence
Threat intelligence (TI) has gained a lot of fame lately, yet it is still a very young concept. There aren’t many organizations who run a fully integrated TI environment in the heart of their security strategy. Likewise, security professionals are still having a hard time to find a streamlined approach to implement Threat Intelligence and potentially leverage the advertised benefits.
Today I want to talk about some key elements that would play an important role in implementing Threat Intelligence correctly. But first, let us position the TI concept inside a security strategy.
Let us start by asking ourselves, what we have without TI?
As a five stars secured organization, we surely have a strong security strategy with multiple processes running altogether to protect our valuable assets. We have the latest IDS/IPS appliances, the brand new SIEM technologies to ingest our tremendous number of events per day, and we enjoy our fully automated vulnerabilities scanners we do run gloriously every week. We also have a state of the art SOC with security analysts and response teams working all together to defend the organization. Yet we are still feeling that it is an overwhelming and not very lucid strategy. It feels like there is something missing! So, what we may be overlooking?
What would we need?
Sure, the obvious answer as our subject hints, the requirement here is to implement Threat Intelligence. More specifically, a Threat Intelligence implementation strategy.
Ok, but what is Threat intelligence?
As TI is still a pretty developing concept, I am not going to dig into its precise and holistic definition. Even vendors as they appear to be racing themselves to provide different solution approaches to TI implementation, a majority of them are still not able to agree on a unified definition of this emerging concept. Conversely, to make it simple, let us consider this definition by Gartner:
Threat intelligence is evidence-based knowledge, including context, mechanisms, indicators, implications and actionable advice, about an existing or emerging menace or hazard to assets that can be used to inform decisions regarding the subject’s response to that menace or hazard. – Gartner Published: 16 May 2013 ID: G00249251
In a nutshell, TI is information that would help us detect menace and achieve a quick and efficient response as a result. Sounds amazingly boring? Yes! Yet doable and efficient when well implemented with automation and run by a qualified team. Now if you always thought Treat Intelligence is a team or a specific skill, don’t start scratching your head and looking outrageously left and right like a fool, it is totally fine.
How can we achieve efficient actual TI implementation?
To implement Threat Intelligence, first, we should make a checklist of what we need for it. In other words, gather information about its main components.
The basic TI environment should involve at least four components which are:
- TI Information (feeds): TI feeds would come from open source communities or paid providers.
- Technology: Software that would help collect and maybe also correlate TI information with internal events.
- Processes: Well-designed procedures and playbooks that will ensure the day to day operations of the TI team and its interactions inside the organization.
- People: A team that will support and operate the TI processes.
Getting started
As a starting point, a good basic understanding of possible Treat Intelligence integrations is a must. This will allow you to imagine fitting basic setup and future evolutions as TI operations mature inside the organization. We can form our first TI integration strategy on simple building blocks that will help us elaborate organization specific use cases, and these use cases would be the base templates for future TI processes designs.
For example, let us consider the TI segmentation as specified in the report “Threat Intelligence: Collecting, Analyzing, Evaluating” from MWR Infosecurity. Threat Intelligence feeds can be separated into four types:
- Strategic
- Tactical
- Technical
- Operational
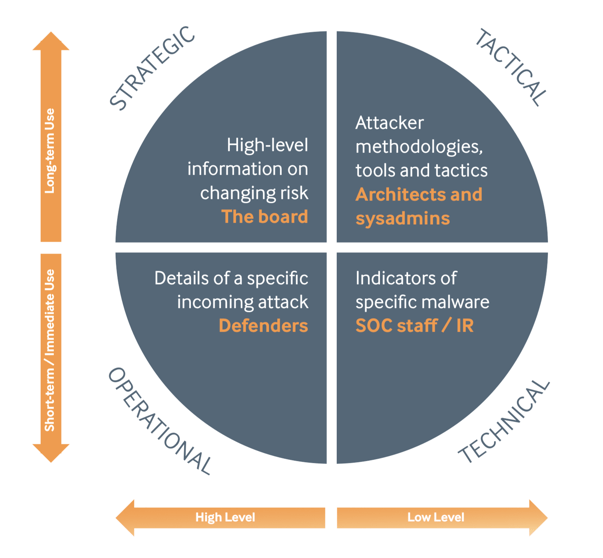
Treat Intelligence types. Source: mwrinfosecurity.com
Here is a quote from the report that will give you an idea about this segmentation:
For example, the fact that hackers believed to be working for a particular nation state have been attacking a specific industry sector is strategic intelligence. The details of their modus operandi, tooling and capabilities is tactical intelligence and can inform defenses, while the list of MD5/SHA-1 hashes of binaries that often appears in appendices is technical intelligence that can be used for investigation.
Some simple steps to implement each type

As a first move, you should start assessing where TI processes may be implemented and take a look at what are the required resources to support it. Will it be running inside a SOC? Or would it better be in hands of a dedicated team? Additionally, it would be very helpful to consult an expert about supporting software and depict possible integrations with the existing security environment.
In the next sections, I will reveal some of the key points to get you started on implementing each TI type as I did advise many of my clients.
Start with strategic TI
Conduct internal workshops with security teams and management profiles to assess current cyber-threats. Initiate TI team into open source feeds to alert and report on emerging threats. For available TI feeds, a little internet search will help to put you on the right track.
Interconnect with other organizations’ TI teams to exchange risk posture reports and get valuable insight that would benefit both parties. This would be basically scheduled workshops, resulting in detailed reports about shared risk posture key elements that may need tracking. Likewise, this would help collect and create listings of all shared threat actors that need specific attention.
Build and maintain operational TI
Design and implement clear and effective TI team operations plan; a TI operations plan should include these elements: work schedules, TI and response teams’ information exchange processes, emergency contact information, escalation processes and onboard involved committees.
Keep an eye on tactical TI
Classify trustworthy sources that would make a home of your daily threat and cyber-attacks news like Twitter and other RSS alerts from security blogs.
Identify interesting tactical information feeds like hacking techniques blogs and other sources. These pieces of information will give TI teams the ability to conduct assessment tests on internal systems to help the response teams to early detection and mitigations.
Implement TI micro-processes in DevOps processes (if applicable) to help build and sustain well secured in-house solutions.
Integrate technical TI
Integrate technical TI feeds into your existing SIEM and IPS/IDS solutions to help reduce “time to analyze” and “time to respond”. TI feeds examples may include updated URL and IP reputations’ lists, suspicious mail attachment hashes catalogs and malware signatures. Read my post on IOCs to get more in-depth with technical TI concepts.
Conclusion
As Threat Intelligence is still in its infancy, a basic implementation and continuous improvement are elected as a valuable approach to a future effective and holistic adoption. Also with this approach, some organizations that still thinking about “where to buy The Threat Intelligence Magic Wand”, can save valuable enterprise budget from being a total loss.
editor's pick
In "Remote Work and Rising Cyber Threats: A Corporate Security Challenge" we delve into the evolving cybersecurity landscape as organizations adapt to remote work. The article highlights a significant rise in phishing attacks, correlating with the shift away from traditional office environments. It explores the vulnerabilities exposed by remote work and emphasizes the need for organizations to update their cybersecurity strategies.
news via inbox
Subscribe to our newsletter and get hot new posts right into your inbox.





