VEVO’s breach! A SOC specialist point of view
It has been 4 days now that OurMine claimed have been able to leak more than 3TB of corporate information’s from VEVO. As you probably already know, OurMine’s recent targets included also WikiLeaks and HBO among others and they even took over Mark Zuckerberg’s Twitter account. The reasons for OurMine making Vevo’s breach public have been clarified buy the group itself as npr.org said on a post: for OurMine it is the result of a regular pen-testing session on random targets that the group maintains monthly.
But one piece of information that opened my eyes on a very important subject lately is the response that the group was given by one of the Vevo’s employees: “F*** off, you don’t have anything,” when the group tried to alert Vevo of the breach privately, as they claim on their website. As a SOC specialist working with large companies on a day to day basis dealing with different InfoSec challenges, this striking response and behaviour from a large company’s internal, made me rethink an important aspect of cybersecurity processes which is: data collection. More precisely here, I want to talk about the various data sources that any company’s SOC strategy relies on.
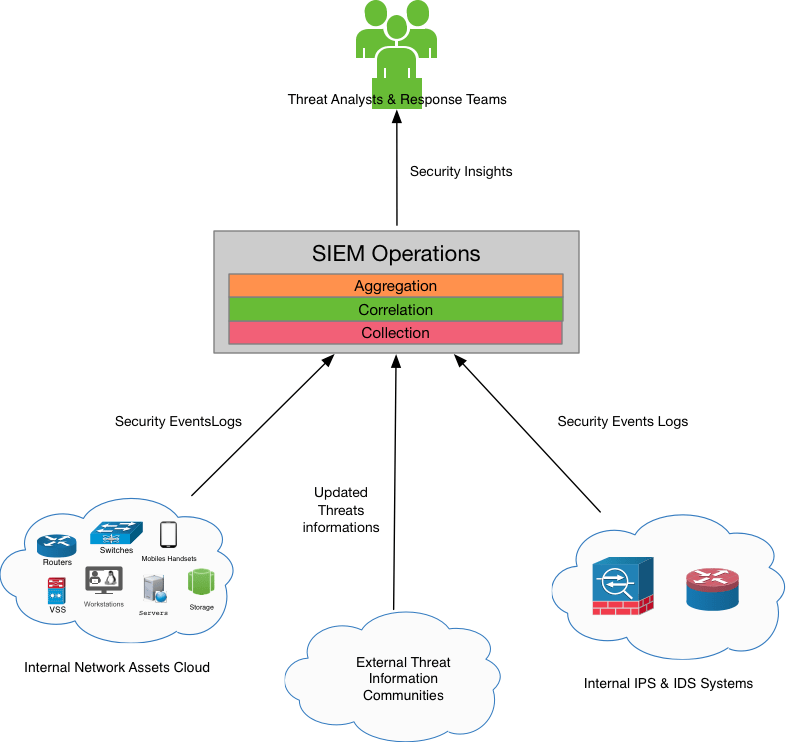
If you are not familiar with what I am talking about, a SOC stands for Security Operations Center, and it is by definition the central point of security data collection, correlation and analysis to help drive APT (Advanced Persistent Threats) team responses and support other cybersecurity processes that a given organization may run. Here is a quick zoom on what it looks like from a logical point of view:
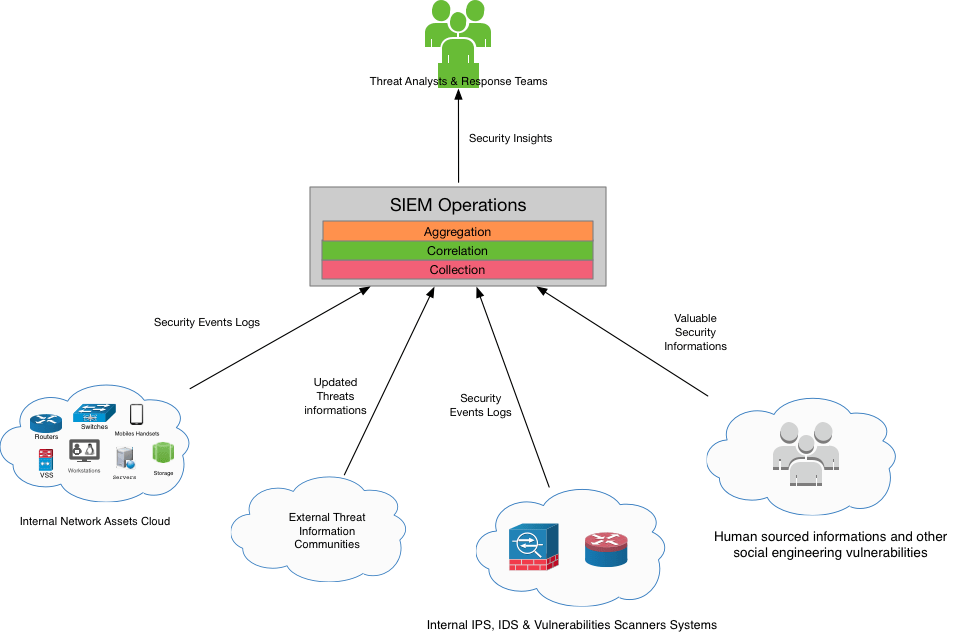
As you can see in the figure above, the various data sources are considered the raw materials in order to maintain the SOC operations working and deliver the expected results when responding against APTs. Now the question is: what if the message sent from OurMine saying that they did manage to break in could have been treated as a log row from an IDS appliance? Wouldn’t it be better if the guy who received the message just forwarded the conversation content to the SOC analysts for investigation? OurMine in this case would have been a great data source, isn’t it? The figure with the new added data source would be something like this:
You would say that the kind of information OurMine provided to Vevo is not going to catch the live events when the attack was happening, but if we take into account that historical analysis is key to confirm and respond even latterly (that is even the point of APTs responses), this would greatly enhance the SOC efficiency when it comes to delivering insightful information for the response teams, since it is already grounded on a scoring engine that work on a credibility basis.
I am starting to imagine a lot of other related data sources that would be of great value for the overall cybersecurity strategy of a given organization. Such data sources would be social engineering weaknesses that automated vulnerabilities scanners would not discover! Should we consider thinking about how such information would be collected, represented and processed throughout the whole enterprise SOC operations? If yes how? Would that have helped Equifax avoid the latest dishonour initiated through a LinkedIn scam?
OurMine said: “We are doing this to improve the world security, as we said before we start all the hacks we did. No one is safe from hackers, even us!”
Well, for me they could, but only if we can shape the operations of Cybersecurity in a more precise, insightful and holistic way.
editor's pick
In "Remote Work and Rising Cyber Threats: A Corporate Security Challenge" we delve into the evolving cybersecurity landscape as organizations adapt to remote work. The article highlights a significant rise in phishing attacks, correlating with the shift away from traditional office environments. It explores the vulnerabilities exposed by remote work and emphasizes the need for organizations to update their cybersecurity strategies.
news via inbox
Subscribe to our newsletter and get hot new posts right into your inbox.