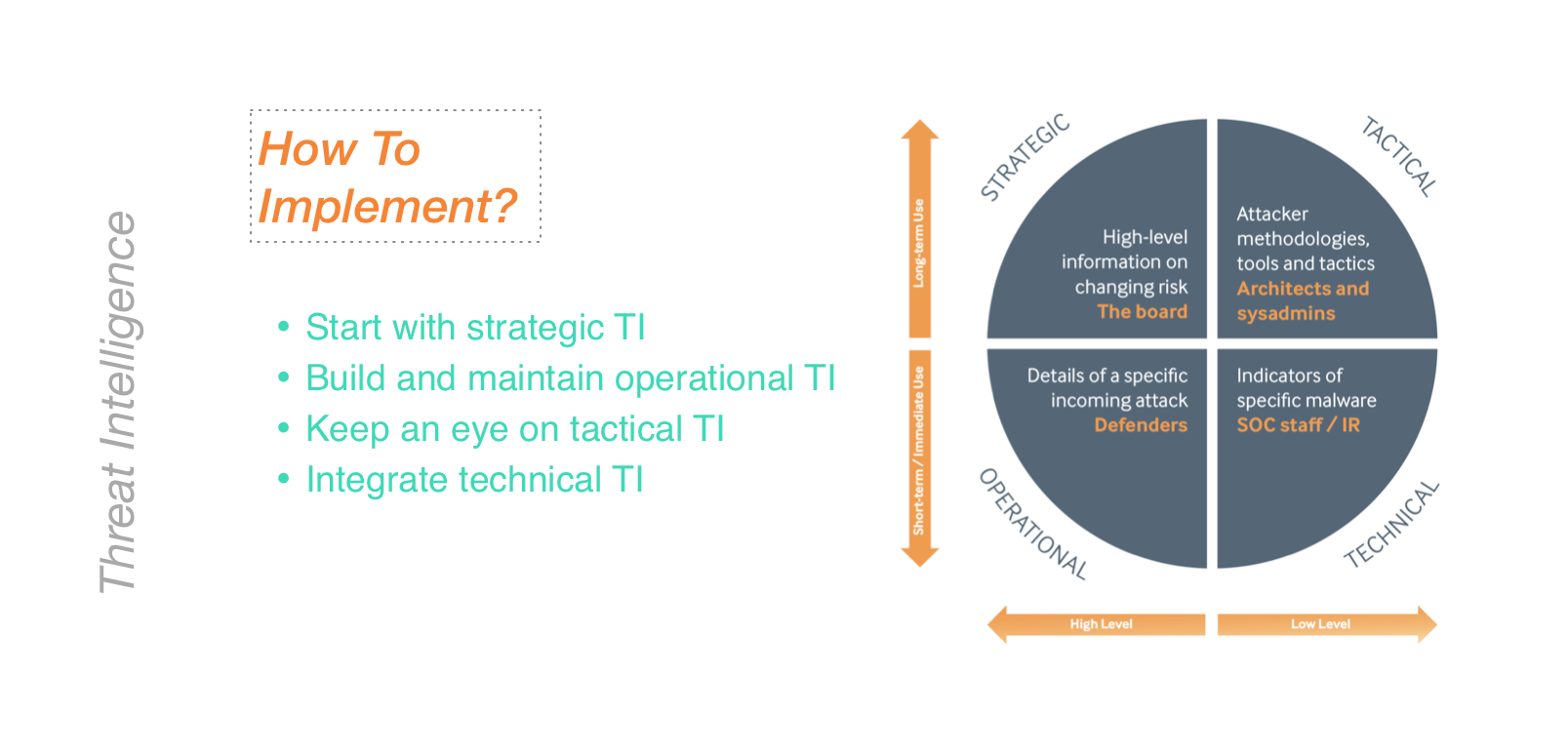
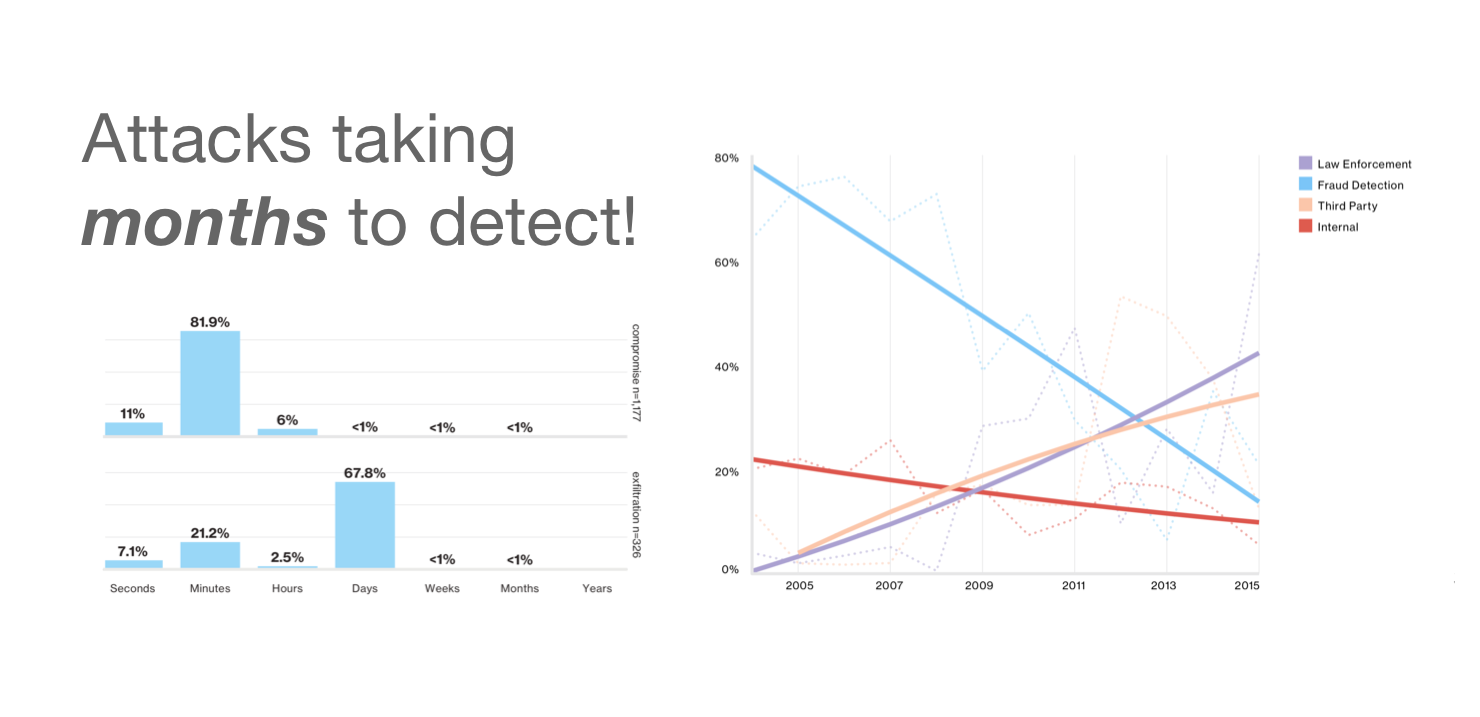
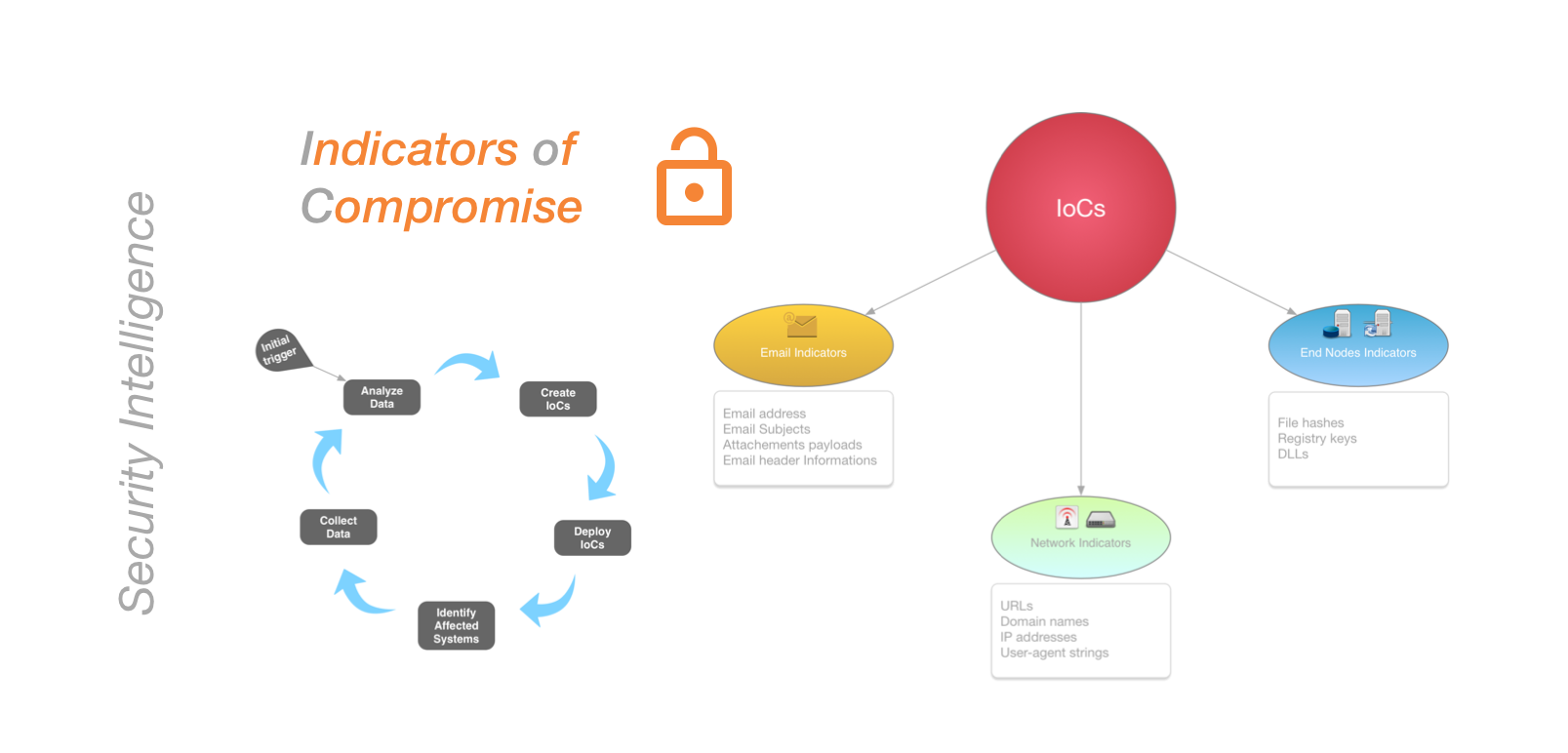
Should we review our cybersecurity basics?
Only a few minutes before the end of 2017, a heavy year on cybersecurity from huge breaches through ransomware spreading and new vulnerabilities disclosers, to new defense technologies loudly evolving all around. I feel however almost tactless when I look the other way around and try to depict all of this in the real-world projects […]